Understanding PCI DSS Certification, Compliance, and Assessment in Every Detail
PCI DSS Certification
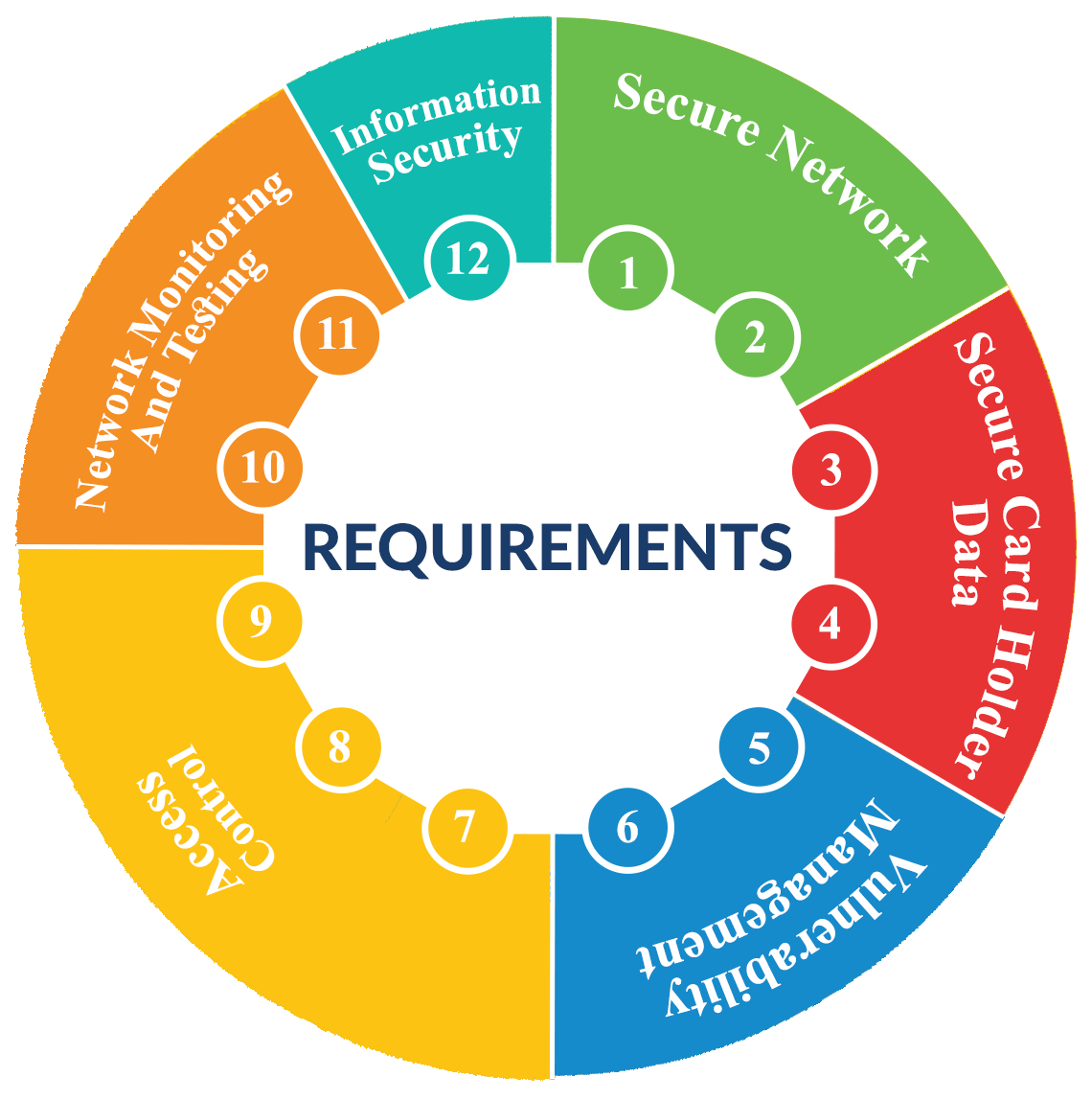
The Payment Card Industry Data Security Standard (PCI DSS), a set of security requirements, must be followed by all companies that accept, process, store, or transmit credit card information. PCI DSS audits are conducted to evaluate a company's compliance with these standards and to identify any systemic weaknesses that could lead to a data breach.
PCI DSS assessments are typically carried out by a qualified security assessor (QSA), who has obtained PCI DSS training and has the relevant skills and knowledge to assess a company's processes and comprehend all requirements for PCI DSS certification compliance. The QSA will carefully review the company's current systems and practices, along with its communication networks, data centers, applications, and databases, to look for any potential weak points.
The QSA will also look at the company's policies and practices with regard to data security, including their techniques for managing and conserving data, lists for controlling access, and security measures. They will also assess how well the company can recognize, thwart, and react to safety threats and breaches.
After the assessment is finished, the QSA will provide a report outlining their conclusions and recommendations for improving the industry's security posture. Any discovered security holes will also be listed in the report, along with advice on how to fix them.
Why Are PCI DSS Assessments Required for Businesses?
Regular PCI DSS assessments should be conducted by businesses to ensure that their policies and systems meet security standards and to identify and address any vulnerabilities before an attacker can exploit them. Failure to comply with PCI DSS prerequisites may result in severe financial penalties and harm to a company's reputation.
Self-assessment, an evaluation of the relevant evidence, an on-site evaluation, the creation of a report, correction, and reassessment are the steps in the PCI DSS assessment process.
If the company is discovered to be in breach of the PCI DSS, it must adhere to the compliance recommendations. This might entail adding new security precautions, updating rules and guidelines, and giving staff members more training. The business must undergo another evaluation to confirm its compliance with the PCI DSS after implementing the appropriate adjustments.
The company will be given a PCI DSS certificate if it is found to be compliant. If it is still non-compliant, remedial actions must be taken until compliance is achieved.
Companies that admit, process, store, or transmit credit card data must go through PCI DSS certification evaluations to ensure the security of their systems and prevent data breaches. For the preservation and protection of sensitive customer data, regular vulnerability assessments and remediation are required.
Multiple Uses Of The Molybdenum Disulfide Nanopowder

Molybdenum Disulfide Nanopowder | images. cdn11.bigcommerce.com
Molybdenum Disulfide comes in several forms like liquid, crystals, spray, powder, or nanopowder. It depends upon the specific requirements and the type of surface.The substance containing the nanoparticles of the original metal is known as the Molybdenum Disulfide Nanopowder.
The usual size of each nanoparticle is around 100 nm. Moreover, it is important to check the purity level before the final use. You can obtain the powder in 99.95% pure form. Therefore, the effects of such a lubricating material are tremendous. It has all the properties just like the Molybdenum Sulphide in the raw form. However, this Nanopowder is more effortless for quick application.
You can use this highly efficient film of lubricant for multiple areas. Furthermore, it is a great stable substance concerning thermal and chemical reactions. The physical properties of this nanopowder work brilliantly in very high temperatures. Also, it is a fantastic catalyst in various reactions. So, you can rely on the material for creating and manufacturing new tools and equipment. The friction coefficient is also low in this lubricant.
Applications Of The Nanostructures Of MOS2
The crystal structure of the metal becomes a hexagon composed of the S atoms. The original family of it is the Transition Metal Dichalcogenides or TMD. The chemical formula of this class is denoted by MX2. In this form, M is the atom and X denotes the chalcogen. So, in a combined effect, we get the chemical formula of Molybdenum Disulfide to be MOS2.
After an intensive study of more than 10 years, researchers are happy to announce the varied applications of the Molybdenum Disulfide Nanopowder. However, the list is not conclusive. This implies that in the coming years, you are going to get more applications of the innovative lubricant.
The applications include the following;-
Photo detectors
Field-effect transistors
Chemical sensors
Solar cells
Valley Tronic devices
Super capacitor electrodes
You can go for processing through different efficient techniques. Some of them are as follows;-
1. Intercalation
2. Mechanical Exfoliation
3. Solvent Exfoliation
4. Vapor Deposition
Thus, the methods can vary, but it brings efficiency in the working style of several types of machinery and other related accessories.
How CPU Trolley Is Beneficial And Important For Secure Motion Of CPU?

CPU Trolley
In the market, there are many computer accessories, which are gaining popularity just because they are convenient in services. CPU is the mastermind of a computer system. And to give proper care to this mastermind we need the proper equipment. CPU isa delicate part of the computer; if any jerk is forced on thispart, then we can lose proper functioning of a computer system. In many situations we must carry CPU you from one place to another. For such shifting, we require some specifically designed CPU holders.By using this computer accessory, we can reduce the risk to the CPU system.
One such CPU protector isthe CPU trolley. If you want to take your CPUfrom home to the office area, then this trolly is going to be of immense use. These CPU holders are available with tyres to give a safe movement to the system. If you are planning to purchase any such kind of service to make your work convenient then initially you should check the quality of the trolley. These trolleys are available with an adjusting nature and can be adjusted as per the model of the CPU.
Key features of CPU holder
CPU holders are the best service to keep your computer system safe from any kind of damage. These holders are available with high-quality materials and tyres attached to their bodies. This service will never let your expectations down. As now all kind of business requires computer systems with every employee. To keep their important workstation accessories safe we must give it well and protected service.
CPUtrolleyhelps to protect the CPU from falls, mishandling and jerks.
It holds the CPU firmly and secures it from any kind of damage.
it helps to make CPU action easy and safe.
these are easy for portable and flexible on floor movement
these are built with space to kept all the cable accessories intact in the holder
it's also built with specific space to put monitor printer or keyboard into the CPU trolley with safety.
There are a variety of CPU holders and trolley only with one motive to increase the safety and secured motility of in computer system. Manufacturers are focusing on different and efficient designs of CPU trolleys. These trolls are easy in mortality and carry water proof qualities in them.
Why You Should Use the Kitchen Cleaner More Often

Imagine a kitchen wherein your garbage disposal gives out that rotten smell and the bacteria keep on crawling within the sink. You will start hating the idea of entering the place regularly.
Organizing and cleaning ought to be performed religiously as it turns uncomfortable and chaotic when you keep your kitchen dirty and disorganized. It is truly crucial for you to set some time for removing unwanted stuff and dirt from the kitchen. To keep your house comfortable and clean, you must urge your family members to take some initiative.
Cleaning has been a very daunting task that you ought to perform all the time. The primary objective of cleaning the home and keeping it organized is to turn your residence more organized and appealing to ensure relaxation and peace for the insiders. The internet is likely to show you through several expert tips.
Using the Kitchen Cleaner and a Brush Helps in Keeping the Space Healthier:
Driving Much Effort
Keeping the kitchen clean may seem to be an uphill task for you if you are not too keen on cleaning your utensils regularly. Your kitchen stands unsafe owing to its dirt when you keep it messy. It contributes much to the overall well-being of your family when you maintain cleanliness inside the kitchen.
Cleaning the overused portions of your kitchen is quite important prior to cooking your food or meal. Kitchen maintenance and cleaning might not seem to be an aspect of great importance, but you must preserve your family health.
Ensuring Health and Safety
While inside the kitchen, you must lay your focus on kitchen cleaning. By disregarding the condition of the kitchen, individuals inside the premises are at a danger of turning out to be sick because of the state of the space.
Fluid spillages can undoubtedly cause an injury if unattended. Old food that has been left in utilized porcelain and on seats can after some time amass various microorganisms. At that point, sandwich presses, toaster ovens, pots, and ice chests may even seem perilous for all members of the family.
Keeping the Hands Dry
It's exceptionally simple for hands to spread microscopic organisms all around the kitchen, since we contact such countless things, from food items to refrigerator handles, aprons to can poppers. So to keep your kitchen healthy and dry, you need to keep your hands clean.
Dry your hands after your rinse it thoroughly to get rid of the kitchen cleaner. In such a case that they are wet they will spread microscopic organisms all the more without any problem. The most secure alternative is to utilize expendable kitchen towels, in any case, utilize a towel that you just use for drying hands – not your cover or a tea towel.
Ensuring Cleanliness
Inability to clean your kitchen might bring about the spread of microscopic organisms and germs, which can make you and other family individuals, become sick. In addition to the fact that you should routinely wash ledges, tidy your floors and up the dishes, however you ought to likewise disinfect kitchen regions and cooking wares that you use to forestall the spread of microorganisms.
Why Pay More Attention to Kitchen Maintenance
You can ensure a longer utility span for the floors, cupboards, and appliances besides ensuring a more appealing look with regular cleaning. The repairs and maintenance costs that you bear for protecting your floors, cupboards, and appliances can be curbed if you remove the build-up and residue thoroughly. It will even keep the functionality of your appliances intact.
You must remember that an untimely need for replacing it may occur when you do not keep the cupboards and floors clean. The fact that your food gets cleaned inside the kitchen makes it reason enough for you to keep the place under all circumstances. A few harmful things like cross-contamination and food poisoning may happen when you do not pay heed to kitchen maintenance.
Putting all things in the appropriate place seems crucial while arranging them inside the kitchen. A deep cleaning practice needs to be ensured inside every kitchen. You may take up the kitchen cleaner during weekends and urge the other members of your family to lend a hand. This way, you can enjoy an organized and clean home for the year round.
Knowing VAPT As Well As Its Advantages For Your Company

VAPT services
Vulnerability Assessment and Penetration Testing (VAPT) is indeed a wide term that refers to a variety of vulnerability management solutions aimed at identifying and mitigating cybersecurity risks throughout an organization's IT infrastructure. It's critical to know the many types of VAPT solutions as well as the variations among them in order to choose the correct form of evaluation for the business size. The Virtual Group provided a penetration assessment, which would be a type of actual testing used to assess the safety of an institution's IT networks and crucial databases.
Because VAPT exams are so varied in terms of depth, width, range, and cost, this knowledge is essential for ensuring that tests provide the most bang for the buck.
What exactly is VAPT?
The testing phase that is aimed to uncover and help fix cyber safety vulnerabilities is referred to as VAPT. VAPT could represent a variety of things depending on where you are in the world, whether it's a catch-all term for several different services or even a singular, bundled product. VAPT could encompass everything from automatic vulnerability assessments through human-led penetrating tests and red squad activities overall.
What are the Benefits of VAPT?
In-depth VAPT services of IT equipment provide insight into the efficiency of existing security mechanisms.
The capability of networks defenses to identify and react to threats is being tested.
Allows for targeted investment to safeguard the IT system, leading to a higher return on investment.
It aids in identifying and securing security flaws.
Instead of focusing on and prioritizing fake encounters, concentrate on and prioritizing high-risk and dangers.
Additional Software Examination to learn about the flaws in the system.
What is the purpose of VAPT services?
Because hackers' tools, strategies, and processes for breaching networks are always improving, it's critical to evaluate your company's cybersecurity on such a frequent basis.
VAPT assists within the safety of the business by offering visibility into security flaws as well as advice on how to remedy them. For companies who desire to comply with regulations, VAPT is becoming extremely important.
What Are the Important Goals Of IS Audit Services?

IS Audit Services
The proper and up-to-date information system of the organization forms its important base. The organization should keep its information system secured so that it can understand its potential risk. Once these risks are identified, they can be tackled to keep the functioning of the organization secured. The organization should keep the check of its information system management, its security, and functioning.
Need for IS audit:
The organization spends a large amount of money in developing its information system (IS) and technology. The main aim of this development is that protects data and cyber security. It is important to carry out the IS audit as these audits help to check that the IS is secured and properly managed to avoid cyber-attacks and breaches. These audits help to identify the loopholes in the IS infrastructure and helps to strengthen it. Different companies provide IS audit services.
Key areas for IS audit:
It is the function of the IS audit services to look at the information system in the best possible way to get the best results. The different key areas looked after by the IS audit services for the betterment of the company include:
Maintaining security and privacy: one of the key areas looked up by the IS audit services is to identify the information leakage and to prevent this data loss. It needs to consider the security involved in the case of management of biometrics, identity, and changes in staff details taking place.
Data management: This area involves the management of data privacy, data access, and data quality.
Flexibility and continuity: It is important to check for the IS continuously. In case of any failure, it is important to recover from the IS failure. There should be scope to identify the scope for flexibility and preparedness, drills, testing, and simulations to develop the company's information system infrastructure.
Fraud management: This area includes IT forensics and fraud risk management.
Payments: IS audit services should also consider the payment risk management, preparedness for the PSD/SEPA, and sanctioning of OFAC.
Protects and testing: This area looks into points like management of tests, implementation of different tests for improving IS, and project risk management.
Contracts: It includes management of supplier risk and considering the risk in contracting.
Information technology controls: This helps in understanding and controlling the changes, management of technological risk. Organization level risk management and Internal IT audits.
Goals of IS audit services:
It is important to understand the requirements for having a well-secured IS for any organization. Reduction of the cost related to IS and helps to add in company profit.
Ensuring information confidentiality, availability, and integrity.
Assessing the ERP system before and after its implementation
Aligning the IS assessment and strategy.
Maintaining the IS standards.
Considering the different key areas involved in the IS audit and the goals of IS audit services, it is important to carry out the IS audit for enhancing the business.
Desk Port – Make the Best Wire And Cable Management

Desk Port
In this improved world it is highly impossible to imagine employees working without computers. Any small or big projects are done with the help of computer and in fact it is not that simple for people today to complete their daily tasks with the help of this electronic dev ice.
Though computer have good demand all over the world since from the time it came into existence but has time changed there are many changes made in the making of computer and also in complete computer desk out of which desk port is one which is making quite simple and convenient for the people to connect all wires neatly.
The main concept of getting this desk port into existence is to turn disturbed computer desk of messy wires into neat and clear. Whether it is a reception desk, computer desk, u shaped desk or l shaped desk this desk port is now winning the hearts of people with its smart way of arranging all connected wires in a perfect manner.
How useful it is?
Some of the best uses of this desk port are:
Makes your desk more spacious and comfortable
Helps reduce any unexpected accidents like shocks with usually happens with messy wire connections.
Can use all required connections from your comfort zone since it is attached to your desk
Using all the devices like printers, mouse, keyboards, scanners and many other accessories is all possible with simple go.
Apart from above mentioned computer accessory a web application namely net box is also reaching the heights of popularity today where the main aim of this web application is to help manage and document computer networks as an open source.
To address the needs of network and infrastructure engineers this open source web application was specially developed where it also supports the assignments of resource to tenant organizations.
Many experts today are striving hard to make people life more simple and easy by introducing many interesting things and Desk Port is one out if that. Yes, this simple box is now used by millions of people where it is especially designed to provide simple use of connection solutions for PCs, video systems, phones, mobiles and many others.
This impressive pop-upbox console is available in the market made up of many different materials like stainless steel, matt aluminum, brushed brass, matt black finishes and many more. Best quality products helps people enjoy best experience of using this simple product where it have soft opening cover with damper and slide locking system.
To meet the custom configuration of different sizes this product is available in many different modules like 3, 2x3, 4, 2x4 and many more where people can purchase the one as per their requirement.